Home > Security Bulletins >Statement About the Remote Code Execution Vulnerability in Some EG/NBR Series Gateways
Statement About the Remote Code Execution Vulnerability in Some EG/NBR Series Gateways
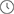 Released on: July 24, 2023
Released on: July 24, 2023
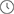 Updated on: Aug 11, 2023
Updated on: Aug 11, 2023
Vulnerability Description
A remote code execution vulnerability exists in the EWEB management system of some gateway products of Ruijie Networks. Attackers may exploit this vulnerability to obtain access rights using front-end codes, and conduct attacks after controlling a device.
Affected Products and Versions
The following table lists affected product models and versions.
| Affected Model | Affected Version |
| RG-EG2100-P V2 RG-EG3230 RG-EG3250 RG-EG3000XE RG-EG2000CE RG-NBR6120-E RG-NBR6125-E RG-NBR6205-E RG-NBR6210-E |
Versions earlier than RGOS 11.9(1)B11S3, Release(07242723) |
Double-click the image to view the complete spreadsheet.
Vulnerability Level
CVSS: 10.0/AV:N/AC:L/Au:N/C:C/I:C/A:C
Solution
Upgrade the device to EG_RGOS 11.9(1)B11S3, Release(07242723) or a later version. You are advised to upgrade it to EG_RGOS 11.9(6)B17, the latest version on the official website.
Version download link: https://www.ruijienetworks.com/resources/products
Ensure that access control is properly set to restrict web management permissions and allow access only from specified trusted IP addresses. Change web management, VPN, SSH, and Telnet passwords.
Workaround
1.Restrict intranet and extranet access to the EWEB management system of the device.
Alternatively, run the following commands on the CLI:
config
control-plane
security deny lan-web
security deny wan-web
security web permit 192.168.1.5 (192.168.1.5 is configured as the management IP address.)
security deny wan tcp port 2060
security deny wan tcp port 2061
security deny wan tcp port 20097
exit
write
2.Change the password to a strong password.
3.Disable local server authentication and screen mirroring, and verify the configurations on the EWEB management system.
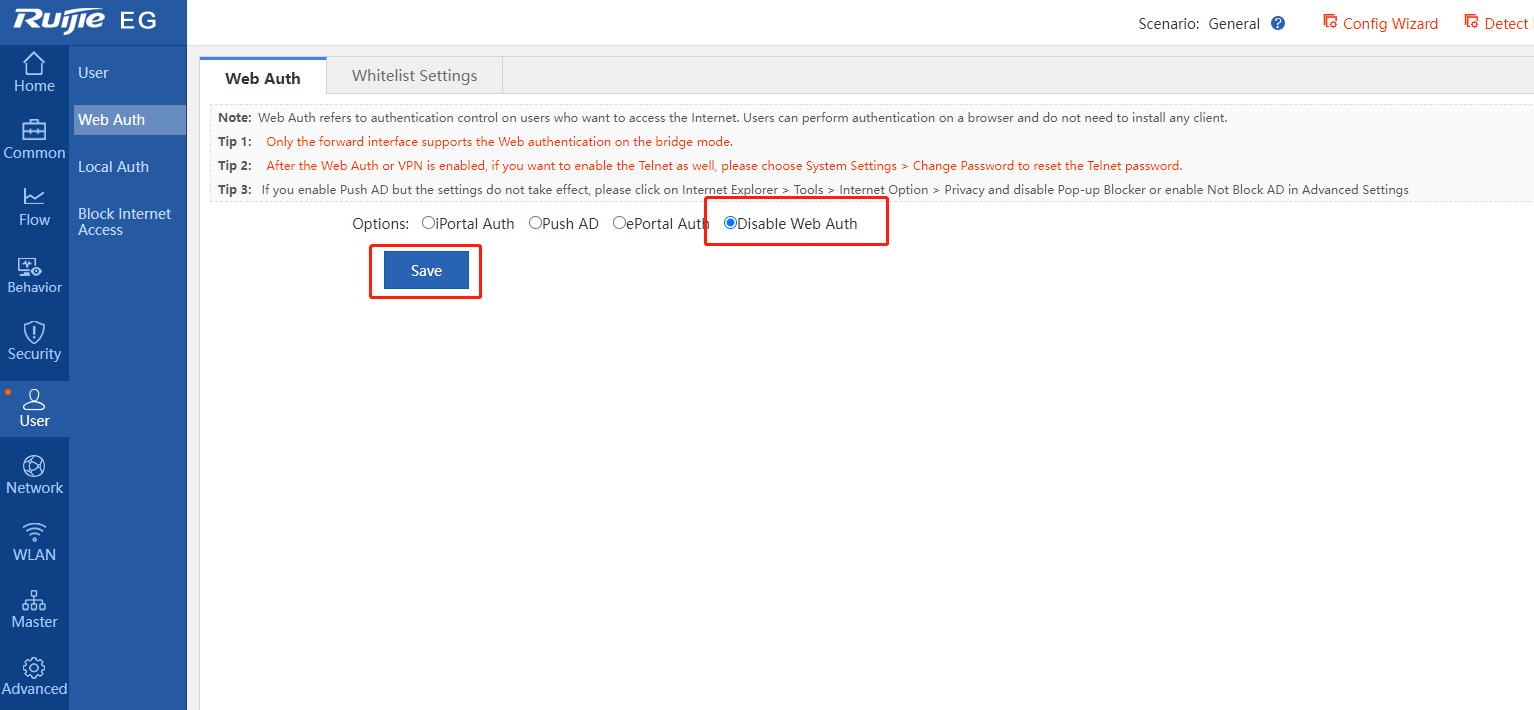
Alternatively, run the following commands on the CLI:
no app-auth local-auth enable --Disable authentication.
no app-auth enable --Disable authentication.
no upnp-proxy enable --Disable screen mirroring.
Service Support
If you have any questions, contact technical support at https://www.ruijienetworks.com/rita.
Vulnerability Response Mechanism
Ruijie PSIRT addresses the reported potential vulnerabilities in accordance with the vulnerability handling process. Learn More
Vulnerability Reporting
Security vulnerability reporters can submit potential security vulnerabilities to Ruijie PSIRT mailbox. Learn More






